- Details
- Written by: Webmaster
- Category: Game Server Setup
- Hits: 851




TLDR - Want a really easy quick fix (CS:S, DoD:S, TF2 and HL2:DM) and don't like reading? Try this below.
Do that first and try more complex methods after that.
Don't know what a Fake game server is? Read this article.
| Finding Fake servers and blocking them in-game | A simple way for most, use a in-game Blacklist. |
| A download that is the result of making your own blacklist | |
| How to make your own blacklist, step by step. | |
| The (early) take away points on making this list | |
| After I wrote the guide I put in notes on tests after a first run. | |
| If the list is too much hassle, there is another way. | |
| Why I found Russian servers were the worst, is it that bad? | |
| Blocking Fake Servers - the ultimate solution. | Unleash the power of your PC firewall! |
| The Advanced method - The Windows firewall (made easy) | We can block IP's and IP ranges in bulk - quickly - all games. |
| Appendix | These are topics that explore in more depth technically how/what scammers use to bait you and fool you. |
| The ports used in Fake server IP's | Looking at why the ports in a fake server IP address are not always valid. |
| Errors that can happen when in Powershell | In the Advanced section we used a script to add IPs, errors can occour |
| Your IP list was working and... now its not blocking IP's. | It can happen, VPN's and other things can stop the IP blocks. |
| Should you use a IP Range or a single IP? | How to decide when to block a IP range, you should use them with care. |
| There are other ways to block Fake Servers. | |
| Tags and what they define | A look at what tags are in different games. |
So a quick fix has to start with a really easy fix and then compliment that with another method.
The easiest fix (for CS:S at least) you can do is mentioned in this reddit post by BallGanda
nosteam,no-steam,nonsteam,fox,perfect,ru,naykon,v34,v93,1mpulse,lkv2,blocker_passes,fastpath,atmmix,rgmix,serverigrcssource
You can add more tags, just a "," and no space separating them. Steam will remember them.
I have a list of what the "Tags" mean in the games that support this here.
To find them just click on the IP Address column title, look at the "Tags" column of the typical fake servers with 100-200 servers under the same IP, see a common tag in them? Add it.
Just be careful you don't add tags that good servers also use.
Will that stop all spam? No.
But it is a valid way to reduce the spam from 11,000 to 300 in some cases. It can also (rarely) remove valid servers.
You can then use the "Blacklisted Servers" method after that to ID, block a IP Range or single IP of fake and bad servers that don't use tags or have ones that valid servers also have.
But you may only have to add one or two IP Ranges.
Basically, look at the server list and...
My list dropped to 212 servers and took only 30 seconds of work.
But those two tasks only work in the single game, like CS:S and others with the server tags filter and Blacklisted Servers function.
For games like CS:S this easy fix is really cool.
Will that work in TF2? Lets see... trade,ru,russian,rus,fastpath That got rid of 60 or so.
Yes, should work on TF2, dod:s and HL2:DM as well but they will be different game to game.
I did generate enough of a list for a download for those that just want a blacklist of bad servers.
Updated 21st Sept 2025 - 197 IP ranges blocked. Version 3.
But I urge you to go a step further and use the advanced firewall method as I will be updating that file.
Just putting a file in a game folder can block 9,000+ servers but... it needs updates as the morons who do this update the fake Server IP's.
Will I regularly update the file above?... likely not. But as you can see I did, from 165 IP ranges to 188 (version 2) in over a week of tests.
Just read below on how you can do that yourself and even apply that to other games like TF2.
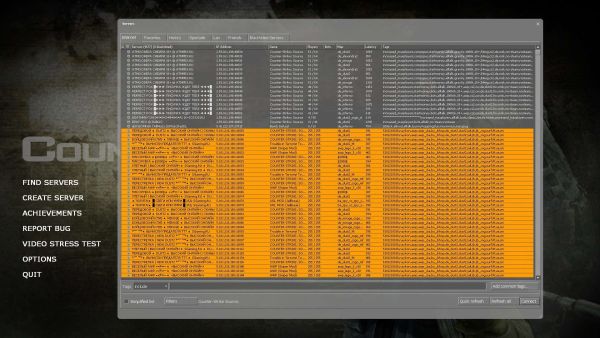 |
| A "Normal" in-game browser that has around 8,000-9,000 fake servers. Complete crap. |
This is a method suggested by Grisha Supersonic in a steam Counter-Strike:Source forum (and others) to block the many fake servers in the Game server browser.
Important: You should note that this is the traditional way, very easy but I urge you to explore the advanced section as we can do much the same but... with the help of another special list I generated, block more of these in a lot more of your steam games.
But first we can do the simple way just for CS:S.
This will take longer to read as I expand out a bit between the steps. In the end after you know what this is, it's actually around 5-10 minutes to first set up then 30 seconds every now and again to keep your server browser clean.
After you are fully informed it is quick and easy. So start the steps and read as you go!
I put in the extra information as not everyone knows why they are doing the step, what a IP address is and what other issues I found along the way.
Step 1.
Open CS:S
Step 2.
Open the "Find Servers" window and view the default "Internet" tab
Step 3.
Make sure you have all the category columns, like "IP Address" and "bots" enabled by right-click on the category title area and selecting any un-ticked ones in the pop-up box. (Click on the image to expand)
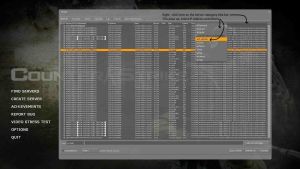 |
| Browser categories - how to select more of them. |
Step 4.
Now sort the list by clicking on the "IP Address" in the category column title.
Note how that sorts a lot of servers with the same name (mostly Russian) and... the same IP but with different ports.
Step 5.
You may notice a lot have the same names and IP's (and different "port" numbers).
A lot of these are fake servers.
Note in most of the ones with similar names or basic IP's (like 5.101.218.188:<different port number>) they all say they are
full of players.
But lets right click on one and view it's information.
Step 6.
Right Click on the server and select "View server info"
Step 7.
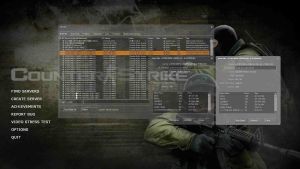
A "Game Info" box pops up, note there is no players listed in the "Player Name" column.
There are heaps of the same IP fake servers too, note in the image below how the IP Address column groups the fake server IP's, same base IP, different ports and slight differences in the name.
Now we can check them as a group, copy part of that IP, alter it slightly and blacklist around 200 fake servers... in seconds.
Click on the image below to expand.
 |
| Identifying fake server groups is helped via the IP Address column sorting. They can't hide now. |
That alone should tell you that the entire 200 or so servers listed on that base IP of "5.101.218.188" are all...fake servers.
Let's look at the IP Address part first so we understand how to block them... in bulk, quickly.
So a "IP" address stands for "Internet Protocol" address.
Like.. 5.101.218.188
A game server will also have a port, it has a :number after the IP...
Like this 5.101.218.188:10003
Basically the 5.101.218.188 part is a server address and the port is a number (:10003) on devices, that is an instruction for devices once they arrive at a IP address.
That part of the game sever IP address (5.101.218.188) can be looked up to find out more.
Abuse IP is a service to find IP addresses doing the wrong thing, scanning other IP's ports that they should not.
https://www.abuseipdb.com/
Put that IP 5.101.218.188 in the search and press the "check" button.
5.101.218.188 is a Russian server from the domain "edgecenter.ru" in the Vladivostok, Primorye area.
Now look below in the Abuse reports. DDoS Attack, port scans, shows a deeper issue.
It is obviously a server that your PC shouldn't connect to.
Now you know a little more, lets simplify a blocking method to make this entire group off your "Internet" tab.
The IP addresses 5.101.218.188:10003 and 200 or so like it can be grouped to one basic address... 5.101.218.0
I simply removed the last IP address number "188" and the port "10003".
That "0" blocks 254 other numbers from 1-255
Lets see what happens in a actual block on "5.101.218.0"
In Step 6 and this step we right clicked on a server that had a huge amount of fake servers with similar IP's.
Do that again.
Step 8.
Right click on one of those servers again like 5.101.218.188:10001 and in the popup box that opens, find that IP address and only copy 5.101.218.
Step 9.
Go to the "Blacklisted Servers" tab, click on the "Add a Server" button
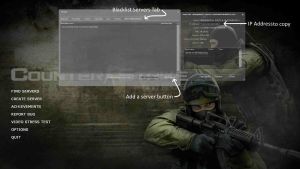 |
| Blacklisted Servers Tab |
Step 10.
Paste 5.101.218. in.
Now add a "0" it's... 5.101.218.0
Step 11.
Press the "Add this address to blacklist" button.
What just happened there is in your game folder... (your drive and folders) Counter-Strike Source\cstrike\cfg a file was edited.
The file in that folder is called "server_blacklist.txt"
This has a set format and looks like this now...
Step 12.
You can now look at your "Internet" tab again, press "Refresh all" button.
Note what it says in the server column now...
"Servers (2706) (199 blacklisted)"
You just blocked 199 fake and likely dangerous servers in your list.
The more basic IP ranges you add the more servers are blocked.
I added another group "5.101.218.0" and the Servers column now says "(9144 servers (600 blacklisted)" ...just from 2 IP groups.
Now use the same technique from Steps 6-11 of clicking on the "IP Address" column finding those large IP groups, right click on the "View server info" and quickly assess if they have players...if not do that same process on the IP by copying the first 3 numbers, adding a "0" after that and blacklisting the entire group.
You should note that there ARE server groups with a lot of valid servers.
The Steam Networking issue.
After you have dealt with some of the Russian fake servers you may also notice servers that have IP's starting with "169.254.X.X".
Look at these carefully, these are not a treat. They all have similar names like "Joey55's Server" and in the IP group "169.254.X.X".
These are players that are using The Steam Networking system and they are either doing that for friends to join or just plain forgot to un-tick the "Use Steam Networking" tick box before making a local game.
Others like a true gaming group with multiple servers and matching IP's are easy to spot too.
They will not claim to have players in the "Players" column that don't check out in the "View server info" check. There will not be hundreds with the same IP, perhaps just 2-7 in the group and likely real players in them.
You can leave them alone... however, clicking on the server group and noticing the same names on all the servers...obviously... this is another problem of fake servers likely with bots and names taken from real players steam ID's so blacklist them too.
As I said I put in another IP group (range) "2.59.161.120" and checking the server info had issues where all players were the same on different servers.
 |
| Two different servers with similar IP's... both have the SAME PLAYERS! |
How about the Abuse IP report on "2.59.161.120" ?
Again a Russian server in Kemerovo, Kuzbass and its complete crap and a hackers home.
You can see how this complex task...can be simplified after you understand the complexity of the IP addresses, how they work and how...you can spot and blacklist these hackers at least with a few steps.
Hope that helped explain this issue and if you are shocked by the results, don't be.
Just note the countries ISP IP ranges involved here, most are Russian.
That country, it's entire internet is censored, controlled by it's government who are also... not to be trusted. It isn't just my opinion... for this issue this just makes you hate the Russian people that little bit more.
If they wanted some PR... not doing things like this would help. They don't so... that forms your opinion.
You can take this a step further, IP blocking is very powerful. You can use them in Browsers, anitivirus, windows firewalls and even on your own router.
Just be careful blocking entire IP ranges (groups) like this, you may be blocking an ISP and valid contacts and websites.
But for a game... this really isn't a issue and you can visit your "Backlisted Server" tab and unblock anyway.
There are pre-made "server_blacklist.txt" for various games but they will go out of date as a scammers apply new IP groups.
Here is one... https://github.com/Ballganda/css-server-blacklist/tree/main
Basically you download the "server_blacklist.txt" file and read the readme on how to add it.
I prefer the method above, even though some of the addresses I found are in that file.
My list (so far in this guide) of blocked servers ranges after using this method are..
2.59.161.0
5.101.218.0
5.189.201.0
80.90.182.0
90.156.230.0
91.230.211.0
91.243.84.0
92.38.130.0
194.135.25.0
194.38.8.0
193.124.9.0
192.124.171.0
188.240.213.0
But... there are more.
So nearly all of those IP's were Russian. Most when looked up on the Abuse IP pages were a problem.
So after adding them, taking around 5 minutes using the quick steps of sorting my "Find Servers" columns and blacklisting this is the real story...
Servers (153) (4299 blacklisted)
Pressing the "Refresh all" button does take a while (it renames itself "Stop refresh" when refreshing)
Now there are more fake servers, Servers (4258) (5468 blacklisted)
Doing the same checks again...Russian IP's, Russian server names spam the server.
Obviously Russians also use Belarus IP's as well.
More to block, lets continue.
213.189.216.0
Adding that one and refreshing I now have Servers (4068) (5669 blacklisted)
You can see the hackers are constantly screwing up the browser and more are added as you refresh. That's natural as servers come and go all the time.
There is a limit of doing this refreshing, eventually all the servers will get found and blacklisted.
Lets add more, this time if it has a Russian name... blacklist it anyway.
After investigating yourself I'll bet you will likely say... "Screw Russian Servers and even if they are real... don't want them on my server list anyway." It's OK, we will get our revenge.
5.181.252.0
45.144.175.0
80.85.156.0
80.87.98.0
80.87.108.0
88.151.117.0
91.226.81.0
95.170.124.0
146.185.196.0
147.45.102.0
147.45.211.0
195.62.52.0
185.41.162.0
194.87.128.0
194.55.238.0
193.108.114.0
178.250.186.0
166.88.182.0
166.88.164.0
So OK.... after those I don't have Russian names and without a refresh I have Servers (288) (9449 blacklisted)
On a "Refresh All" button, it took 2 minutes and new total is Servers (262) 9425 backlisted)
Similar but you can see differences.
Any new Russian names?
No.
Any of the large amount of similar IP's with different port numbers?
Yes but... they are an actual server groups doing the quick checks of filtering the player numbers in the "Players" column and right clicking "View server info" and seeing the same data and actual players.
Refresh all again... Took another 2 minutes and now I have Servers (296) (9442 blacklisted)
A similar result.
So far I have struggled to find a Russian server that isn't involved with a bad IP and fake servers.
Going to the web based lists I see this at the same time 122 server online 122 players on their list...
https://www.steamserverbrowser.com/games/counter-strike-source
These lists update at different times and will never be exact to the in-game list and also that in-game list is not counting actual total players... also some server may not show there from bans.
Nor can I find Russian servers... I don't wonder why seeing they are filtering for fake servers.
So, this method can reduce those fake, spam, servers and also you may want to check another article on servers doing the wrong thing.
In that one I had a example group "FastPath" it too has a IP you can put in the list because of the scams they operate and also they hack other servers, scanning ports and hacking other servers in the Abuse IP check... add this too...
164.132.201.109
Note I didn't remove the last IP number in this case as all Fastpath game servers are that IP...just different ports in the different games they... scam you on.
That is a French IP range and there may be other gaming servers that are not scumbags in that IP range.
That is also another warning, select your targets carefully in a IP range.
If you play other Steam games you will notice they all have the "server_blacklist.txt" file in the game folder...
(Your drive and folders)\SteamLibrary\steamapps\common\Counter-Strike Source\cstrike\cfg
So...copy your file to that game too if it uses the same file. dod:s, HL2:DM will also work.
To find that address for the game, lets use day of defeat:source...
The "dod\cfg" folder is where the "server_blacklist.txt" file should be placed.
To find your dod folder…
1. Open your Steam Library
2. Right-click on the “Day of Defeat: Source” icon
3. Select “Manage” > “Browse local files” ….
4. A folder called “Day of Defeat Source” will pop-up, the dod folder is in there.
5. Now open the "cfg" folder
6. Copy and paste the "server_blacklist.txt" file in the cfg folder and overwrite the file.
If you see your server list getting new fake redirect Russian fake servers... just remember the simple technique of building your own list, updating it as they change IP's.
Leave the older ones in your blacklist, it will not hurt the game. Besides, they may reuse them.
My list ended up 34 IP ranges of complete and utter crap hacking and scam servers that blocked 9449 bad servers and reduced the game server browser list to a list of 200 or so real servers.
146.185.196.0
147.45.102.0
147.45.211.0
164.132.201.109
166.88.164.0
166.88.182.0
178.250.186.0
185.41.162.0
188.240.213.0
192.124.171.0
193.108.114.0
193.124.9.0
194.135.25.0
194.38.8.0
194.55.238.0
194.87.128.0
195.62.52.0
2.59.161.0
213.189.216.0
45.144.175.0
5.101.218.0
5.181.252.0
5.189.201.0
80.85.156.0
80.87.108.0
80.87.98.0
80.90.182.0
88.151.117.0
90.156.230.0
91.226.81.0
91.230.211.0
91.243.84.0
92.38.130.0
95.170.124.0
This method saves a lot of time Grisha Supersonic method is valid and the above proves it is also a huge time saver.
However, even after finding 34 IP ranges that blocked 9,000 + servers, the second run some 12 hours later, new ones in my blacklist doubled and again the fake servers were... Russian and most IP's when checked on Abuse IP... were also into hacking, port scans and other activities.
So is there a end to putting in these IP ranges? Yes, but it's still a bit of effort.
I have ended a week of testing my final list with 165 IP ranges of servers that total anything from 6,000 - 9,000 depending on... a few things.
So once a IP is added, especially since most are Russian and most of the world wouldn't go there anyway, leave it there.
In my list (unlike others) I have placed a name if I found a certain group in the server name. I also explore that next, who are these "people" doing this?
As mentioned before the Fake IP server operators will have automated methods and use other IP's, then on that one IP assign many port numbers. That makes hundreds of servers on the one IP.
Using a IP range block, not only knocks off all the port numbers possible, but also other IP numbers.
You need to be careful to make sure you don't block real servers but at the moment (seeing most are Russian IP's) a quick check on Abuse IP or the various "Whois" look-ups can confirm a "bad actor".
But simply put, on sorting the "IP Address" column of the "Internet" tab, if you see hundreds of game servers with the same IP and different ports, and player numbers above a discrepancy of around 3 or so, then they are all fake... block the entire IP range.
Even if you find a Russian based server name, block the IP range anyway as it may be used in the future.
Just block any new ones as the arrive, seems to work fine...
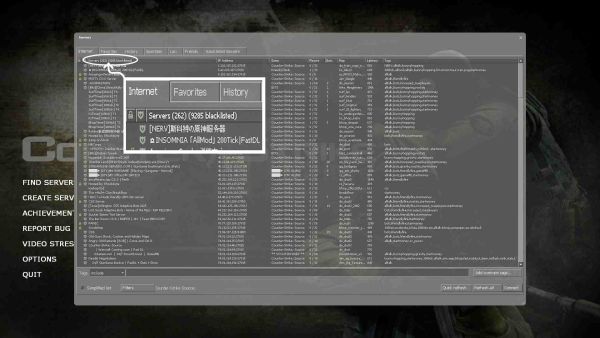 |
| A check 24 hours later - added at least 30 more IP Ranges added - 262 real servers and 9,285 blacklisted. |
Using a quick check of pressing the "IP Address" column and looking for IP Addresses that are the same, I found a new one.
That alone is enough to block that entire IP range. Just by that simple check.
However, to confirm, going to Abuse IP... the IP was used 11 months ago for DDoS attacks, BruteForce, Web Spam.
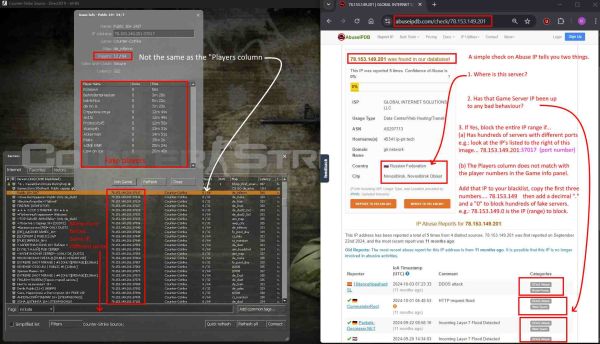 |
| 78.153.149.201 a obvious bad IP, showing every three days or so new IP's come in |
The (multiple) persons doing this have a list of IP's they either compromise (stolen) or pay for the use of a dedicated IP address.
Its a cat and mouse chase, it does not take long to identify these rouge IP's and blacklist the IP range.
After 3 days (above 72 hours), I started to add IP's from CS 1.6, CS2 and TF2. Now some of the TF2 and CS2 new IP's I added could be in my next run but each game does seem to have their unique ID's, e.g.: You don't seem to find Fake servers with 200 servers on the same IP in CS:S and CS2.
After adding more from other games I was up to 383 single IP's and IP ranges in my firewall list.
I waited 3 days and scanned the games again, here are the results
| Game | New IP's added | Notes |
| CS 1.6 | 2 | 8.136.102.78, 5.143.38.1 — classic spoof behavior |
| CS:S | 0 | I was expecting more but none |
| CS2 | 3 | 45.88.90.173, 45.143.203.206, 141.105.130.109 — high saturation |
| TF2 | 4 | 108.181.244.74, 108.3.170.18, 185.211.51.x, 193.38.251.x — CIDR clusters |
That was a surprise... that indicates...
So far the tests indicate that the spammers may be timing their fake server IP's and rotating them over a time period, say every 3 days or a week they will rotate and remove IP's and add another set.
We have to remember that they have many to choose from and the ratbag suppliers of cheap hosts are many...at least in some parts of the world like Russia, China, and some EU countries.
Will you eventually find them all?
Nope and hell no.
Just maintain your Blacklisted Servers tab (or any list you make) by hitting the IP Address column and looking for sequential IP's ...especially with Russian names, taking that IP range e.g. : 78.153.149.0 and adding that IP to your blacklist.
There are different methods I use for "scanning the game server browser" quickly, no special tools just... sorting the list via IP Address, using the scroll on the mouse and you can quickly spot 200 or so same IPs as the list does not jitter with the change of IPs... just the ports.
How long apart should you scan your list... not sure but I'll update this section as I do mine but the CS:S IP list has held for 3 days now... however I scanned that game for 3 days and then stopped for 3 days, then found none. So you could say with the sample I have once a week? 30 Sept 2025.
You may be better off going to game tracker or another service like this one, or Game Tracker.com.
They do a decent job if you don't like all this effort.
Just be careful with online game server lists. I noticed the various gaming groups that do use Fake Servers are listed on these lists, even though I put them on my blacklist as it was obvious they have Fake Servers with their name on it.
Now that could also be another issue too. One of the scams these "operators" (morons) use is to grab a well known name, have a Fake Server with that name and redirect you to their servers.
The real issue is, Russian based IP's are out of control, that's the take away from this experiment for me.
It's fact backed by where that Fake Server IP is. You cannot hide that fact.
Seeing the Russian IP's are almost the entire list of blocked IP's, you can easily spot Russian cyrillic alphabet server titles and immediately suspect that server.
I certainly would never join a Russian game server IP after looking at the IP Abuse reports one by one.
It would be better of having the Russian region... as a region you can un-tick in the game server browser on Steam.
That is also going to affect countries like Belarus, Kyrgyzstan and a couple of others the Russians are using.... I see Poland servers are being used by one group SGaming.ru .... so it's not only Russian IP's but is... a Russian gaming outfit.
Seeing most of the IP's I looked at also where listed for Abusive attacks on other IP's, there could be a deeper reason why they are in your game server lists and why... you should spend a little time and block them.
In Australia we have a saying... "Does it pass the pub test?" Now even a group of drunk dudes would look at a fast statistic and say... "Mate, that's just bullshit". Look at the image below taken from a CS2 server list with the country of origin statistics after the country...
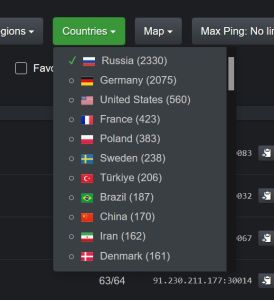 |
| "Mate, that's just bullshit" |
WTF. The stats there.... Russia and Germany both found with bad IP's along with France and Poland with Russian links (also USA and note not all Russian IPs are in Russia physically).
Looking at that over representation of the Russian servers immediately looks suspicious... even if you have finished off a dozen beers and you don't play CS2 or use a PC.
But are these Russian groups the only bad gaming groups doing this?
No.
I found bad behavior in France, Ukraine, USA, Argentina, UK, China... these groups offer "Premium VIP membership" special "perks" (some perks you can regard as admin cheating) and other pay for services that may give a player an advantage over others on the server.
The way IP allocation works does not mean the Russian IP is within a actual countries border. It can mean 5% or so are not actually in the countries actual borders.
These Fake servers are often connected to IP's that scan other game servers for players Steam ID's and other info' and that comes up in the Abuse IP reports... other game server operators reporting that game server IP has hacked , DDoS attacked or port scanned their server.
Facts remain, a lot are Russian IP's and up to no good.
This is the best, its not only for CSS but for a lot of other titles.
This is a known method and in other guides see here for them. Most of them will show how to add IP's or IP ranges to the windows firewall one by one. We can do that faster.
Seeing we (well me) have done the hard work of identifying a bad IP and putting them in a list, we can use that file and grab the IP's, put it in a simple text file and use that for a Windows Firewall.
The advantages of this are, the games that don't have the ability to blacklist the list generated in this method... the bad IP's are blocked no matter what game server browser you use and what game you are in.
I will only use Windows 11 here as Windows 10 is about to...die at the time of writing. I would say you could also use this on Linux but that would be a very different set of instructions.
Disclaimer: Don't be sloppy, BUT don't be afraid to try this.
The word "advanced" is on purpose, this really is a advanced step normally used by advanced users, follow the instructions WITH CARE and you will be fine... BUT if you don't READ ALL OF THE GUIDE then ... something bad or more likely nothing will happen to block IP's.
In saying that I have wrote this guide so any normal windows user can do this and... it takes longer to read than do in the end.
Plus you may learn a new basic Windows skill.
Using a downloadable test file I have already assembled dodbits_steam_server_ip_blacklist_cidr_v1.txt (updated 10 OCT 2025) we can stop scam and VIP-linked and otherwise Fake Servers across a lot of steam games.
Keep in mind that the test file while it does do a Windows 11 system wide IP and IP range block and can block bad servers in other games, the list really is only targeting Counter-Strike:Source like we did above however I have also included CS2, CS1.6, HL2:DM, dod:s, and TF2 in a second version of the file 25th September 2025.
Also if a IP used in a Game server is also the IP for a Website then that is blocked too in a windows firewall list, e.g.: The infamous Fastpath game servers are blocked, so is the Fastpath.fr website. It is a stupid thing to have a website and a game server on the same IP... goes to show how cheap that scammer group is. Its a scam outfit anyway... and most of the IP's involved here are Russian IP's with a bad reputation so blocking them... good idea.
More on assembling a custom file for whatever game later on, for now lets just block some CS:S and other games bad IP's.
Step 1: Download the Blacklist File
In the download of the test file above, there is a readme on where to put it.
Important note: Do what it says in the download readme as we are going to make some commands and your computer name, the file address in the commands are critical to change.
To convert any commands I make in the guide I will highlight in Yellow what you need to change.
e.g.: my computer name in the guide is "dodbits" if you see that you need to change that to yourcomputer name.
So now you have downloaded the simple text file and placed that in your documents folder in a folder called "1_bad_ip_lists"
Lets continue now. We are about to use the (admin) Terminal in Windows, don't be put off, it will work fine so long as you do this step by step.
Step 2: Open PowerShell as Administrator
On Windows 11, do this:
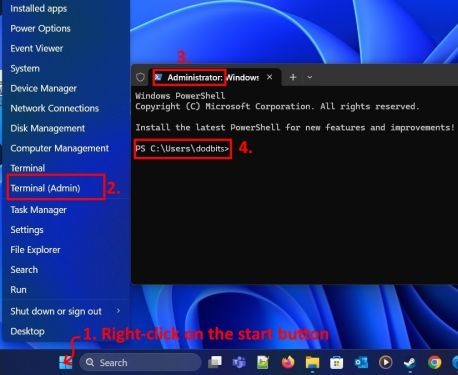 |
| The steps in opening the Windows 11 Terminal (Admin) |
Step 3: Run the Blocking Script
In this step we are going to enter in bulk bad IP's to block to your Windows 11 firewall.
Don't worry if they don't do what you wanted we can remove them as easily as we added them.
Important note: When using PowerShell, if you use right click copy and paste a lot you will have to adjust. If you copy from this website or a text file Right - click copy is not available.... just use the CTRL+V keys to paste. More on keyboard key combo's for windows here.
$ipListPath = "C:\Users\dodbits\Documents\1_bad_ip_lists\dodbits_steam_server_ip_blacklist_cidr_v1.txt"
$badIPs = Get-Content $ipListPath | ForEach-Object { $_.Trim() }
foreach ($ip in $badIPs) {
$ruleName = "Block Bad Steam Server - $ip"
if (-not (Get-NetFirewallRule -DisplayName $ruleName -ErrorAction SilentlyContinue)) {
try {
New-NetFirewallRule -DisplayName $ruleName -Direction Outbound -RemoteAddress $ip -Action Block -Profile Any -Protocol Any
Write-Host "✅ Rule added for: $ip"
} catch {
Write-Host "❌ Failed to add rule for: $ip"
}
} else {
Write-Host "⚠️ Rule already exists for: $ip"
}
}
Next you will see the Powershell window flicker a bit as it is adding 100-200 IP Ranges into the windows system as a group “Block Bad Steam Server”.
Important Note: If you see red text while the list is being added or at the end, your list (if you changed mine) may be structured incorrectly. Look here for more information.
If all went well, when it reaches the last on the list it will look like this….
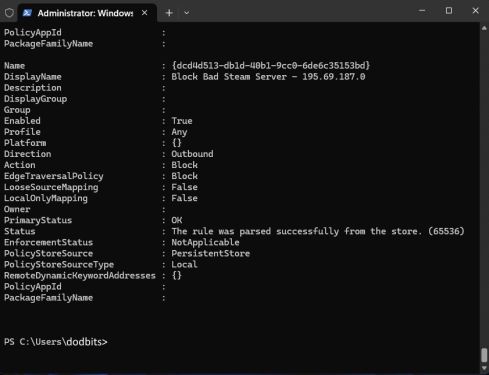 |
| Success! The IP's in the file are added to the windows firewall incoming rule as a bulk list. |
Time to test it now.
Important note: Only IF you have blacklisted CS:S IP's like the above method using the CS:S "Blaclklisted Servers" Tab in-game.
Now if you already added IP blacklists in CS:S you have a file in Your drive and folders...steamapps\common\Counter-Strike Source\cstrike\cfg called "server_blacklist.txt"
You should delete or just rename that file to server_blacklist_BAK.txt before testing.
To continue:
Open your Steam game like CS:S and test the in-game server browser. At the time of writing CS:S was totaling around 8,000 to 11,000 servers, most of them Fake servers.
Does it look like 150 to 300 now when just before it was 8,000 to 11,000 servers?
Well, it works then.
Also test the Steam inbuilt browser in the steam menu select “View” then find “Game Servers”
You have to select a game in the unnamed drop-down box (next to “Friends” button) and then press the refresh icon (two arrows in a circle) to refresh the list.
The main Steam Game Server browser will now be affected by this “windows IP range blacklist” where before... it wasn't.
That is not possible before with a handmade blacklist that only works in games like CS:S, TF2, dod:s and other that have that function.
This IP range blacklist is working from your Windows files, not steam.
You can now see how powerful this list is. You are selecting a system wide list of IP's and IP Ranges you never want Windows to connect to.
Also maybe you can see now why the list you make better not include IP's you want to connect to, this will affect any IP on your PC.
You may want to do this, remove it all and start your list again, no problems it only takes a simple step.
You already know how to get the Windows “Terminal Admin” window up (we did that in step 2 above) so do that again and this time we will paste this in….
Get-NetFirewallRule | Where-Object {$_.DisplayName -like "Block Bad Steam Server*"} | Remove-NetFirewallRule
Press enter.
The terminal window will do some work and you can see that working away.
After its done the activity stops and you will see the command prompt go back to this…
PS C:\Users\dodbits>
To test its really gone just open CS:S and watch it climb back to the 8,000 to 11,000 server stacked with Fake servers.
This may be a bit challenging for some.
So far you have taken my list and learned how to install it into the Windows firewall making a bulk inbound rule of some 200 or so IP ranges.
The list itself requires you to know how to spot a fake server group, investigate it and take part of the IP, the first three numbers separated by a “.” decimal point.
Above I have advice for Counter-Strike:Source and how to do that so if you skipped that in this guide…go read it now.
Now that IP range number that works in the Steam blacklist will not work in the Windows Firewall.
So basically, open the CS:S in-game browser, click on the “IP Address” title to sort the list into consecutive IP’s, one after the other.
Lets say you found a stack of servers, all very suspect as they have around 200 with the same IP…
193.124.9.47
The only difference is the port number is different… heaps of them 193.124.9.47:40008, then 193.124.9.47:40010, then 193.124.9.47:40012 and so on.
They may also have a Russian name, a absurd player amount like 0/255 or 0/64 and even ones that do have players like 233/255 when you right click for “View server info” you find…no players.
OK that IP of the first one 193.124.9.47:40008 we can copy that.
We just need this part…. 193.124.9.
Now add a “0” = 193.124.9.0
That is the entire IP range… we can use that in the in-game blacklist file but the text file for windows we will need to edit again.
We need to add “/24” so now it’s 193.124.9.0/24 and the Windows firewall will look at that and block all IP’s in that range…. That’s a lot of choices that the Fake Server operator cannot use anymore to spam the game Server browser.
Now this next part gets even more powerful and risky too.
CIDR Block Decision Guide: When to Use /32, /24, or /16
First up... whats a "CIDR" ? Classless Inter-Domain Routing.
Just think of it as a group of 4 numbers separated by a decimal point to make a IP address.
There are some \<number> you can add to the last number and add many more IP's in the range...
/32 — Single IP
Range: Just one IP (e.g., 101.42.151.253)
Use When:
In the list put either 101.42.151.253 or 101.42.151.253/32
/24 — Small Subnet
Range: 256 IPs (e.g., 101.42.151.0/24 covers 101.42.151.0–101.42.151.255)
Use When:
In the list after seeing that consecutive first 3 numbers a lot like 101.42.151.23 and also 101.42.151.24 and some more of the last 4th number... then use 101.42.151.0/24
/16 — Large Subnet (use with great care)
Range: 65,536 IPs (e.g., 101.42.0.0/16 covers 101.42.0.0–101.42.255.255)
Use When:
In the list after you find information that MANY bad IP's are the first two numbers, like Russian or Chinese IP's, consider blocking many more potential IPs the scammers may use... then use 101.42.0.0/16
So how do you make these calls?
| Scenario | Recommended CIDR | Why |
| One spoof server confirmed | X.X.X.X/32 | Precise, minimal impact, safe |
| 3–10 spoof servers in same block detected | X.X.X.0/24 | Clustered abuse, safe coverage and can predict 254 others. |
| 10+ spoof servers across multiple blocks detected | X.X.0.0/16 | Provider-wide abuse, future-proofing up to 65,535 more IP's |
To find out about when to use that CIDR like 101.42.0.0/16 you need to look at the provider, look at sites like AbuseIP records.
That listing shows 101.42.151.253 is under Tencent Cloud Computing (Beijing) Co., Ltd. Do a search on them... do they have a bad reputation?
Also, do use the AbuseIP as you will soon see as this one IP for CS 1.6... almost all the bad servers are hosted on tencent.com.
In CS:S IP's using AbuseIP you will also note the same, and also look for the reports below... hacking, port scanning... then... use the X.X.0.0/16 type and the ISP ./ provider is rotten to the core... block any others as you may never play on a Russian server anyway.
In the end its a judgement call. If you get around 100-200 CS:S or CS 1.6 servers after blocking...it s about right. If you see some huge dip below that total server... just review any CIDR types and change them e.g.:101.42.0.0/16 change to 101.42.151.0/24 or... just delete the 0/16 ones and see what comes back.
Normally, once I add these bigger groups... if I did my research I don't remove them and... they predict many new bad IP's.
Back to checking your list.
OK… you go and make your own list… it takes many hours and also many days or even a week as they operators turn these on and off over the week.
They will also make new IP’s and you have to add them, using a new file and running the commands in PowerShell again.
The list itself MUST be neat.
You may find duplicates, mistakes in the format.
Every space, “.” and IP number HAS to be perfect.
You will need some skill here in working with a spreadsheet like MS Excel or a free alternative like LibreOffice.
There are easy ways to manipulate lists like this like the Replace tool…. You need to either skill up in managing bulk lists or… check each line one by one.
Or… just be really neat when making your list.
Adding more IP's later on... is a matter of just making sure they are of the correct format and only one entry per line.
Updating the list you use the same script in Powershell at the top of this "advanced method" guide, it has a check and you will see this in Powershell...
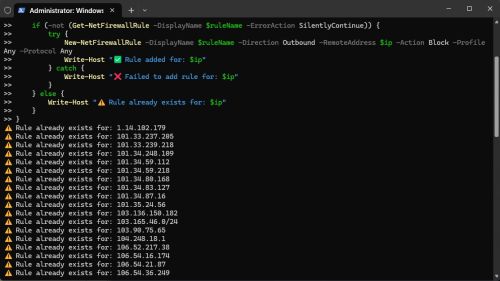 |
| Powershell - adding new IPs, the script will check each one and not make a duplicate. |
Is my list accurate?
For me it is but if you are a member of one of the (shonky) groups doing this and have paid for VIP access to play on a server and kill all the "noobs" (other unsuspecting visitors who got redirected from a fake server) then you may be not able to connect.
Make your own list, mine... is for this guide.
I hope you found something useful there.
You can now maybe see how using the Windows Firewall, you can create firewall rules that can work with not only CS:S but in ALL STEAM GAMES.
You can combine all the bad IP's in one list, if you play CS 1.6, CS:S and CS2... then a combined list will... kill the servers in the various browsers in game and in the main Steam Game Server Browser.... finally that may now be of some use.
Just remember, this method is powerful. It is up to you now to make your own list of IP's to block.
Seeing most are Russian in CS:S and some in a Romanian gamer group that are actual IP's in other countries, you need to be careful in your lists.
Next up we will investigate other games like CS 1.6 and look at WHO is doing the wrong thing, HOW they do that and WHY we should block a IP range, or a single IP.
A section of technical items on blocking CS:S servers
If you look closely at the many consecutive ports and you know about game server ports you will see the ports on a real server are different to fake servers.
Are the Ports After the IP Address Valid?
In legitimate servers: Yes, the port (usually 27015, 27016, etc.) is critical.
It tells the client (your PC) which process to connect to on the host machine (The Game server).
Game servers use these ports to handle incoming traffic, and they must be open and correctly configured for the server to function.
In fake servers (redirect traps):
The port doesn't need to be valid for gameplay—it only needs to be valid enough to appear in the server browser and accept an initial handshake.
Here's what spoofers do:
They run a lightweight listener on a port (e.g., 27018) that mimics a real server.
When a player connects, it immediately redirects them to a different IP:port combo (the real target server).
The original port may not host a playable game at all—it’s just bait.
So yes, the port is technically “valid” in the sense that it responds to queries and appears in the browser, but it’s not hosting a real game session. It’s part of the scam.
In this script there is a check for duplicates that a rule already exists, it is looking for duplicate IP's in your list. You may get a notice at the end hat it found a duplicate.
If you edited my list I urge you to read the section on making your own list.
That isn't all that can go wrong with these rules and your list.
Important but rare note on errors: Watch it as it adds the IP's and look for any "red flash" of text.
That is a error IF YOU CHANGED my default list and got the format wrong.
If the format of the file powershell is reading gets messed up you may see a red flash as it’s compiling the list into a rule.
This happened to me, I had one error on the list 103.90.75.65:0, that should have been 103.90.75.65 a single IP from a Russian gaming outfit battle-strike.ru on a Netherlands (Amsterdam, North Holland) IP that has bad IP Abuse reports… https://www.abuseipdb.com/check/103.90.75.65
The error looks like the below image in powershell and it does not tell you WHERE the error is but it this case it was very near the end of the file and could be 10 or so above the other IP’s before this error message.
That is why a check in the command was added to the initial commands you pasted in.
Here is what a error message in the file looks like in this step... click on the image to expand
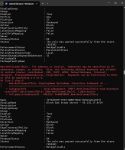 |
| What an error looks like in PowerShell |
To avoid these errors in your file you just have to be careful making your list.
This can be interference from a VPN you just used or other network/system changes.
Normally if you don't adjust network settings this should be rare but it can happen.
Solution 1 : Most issues like this will be solved with a restart of windows.
Solution 2: Maybe you or something else on the system adjusted the Windows Firewall.
Solution 3: In this guide we learned how to download a text file and use PowerShell to apply the IP's. We also learned how to remove that group of IP's from the text file. Maybe recently added a a bad entry in the text file (see above error item) and it has messed up the rules.
First, what is a IP range? For a steam server browser...
We don't need the port number to block just 193.39.68.66
Now in that case I notice in the browser a lot of other severs with the same IP different ports.
Also, I note the names are all different "bc18go.ru" and "ATMMIX.RU" and "PERFECT FOX". All Russian IP's.
They are all this Steam group whom claim to be "legit". They have a website and their servers are listed.
Those "real" server IP are an absolute must to blacklist as a priority. They are the reason the fake server are there.
Ban those and any of the redirect ones you find.... banning those on the website is critical.
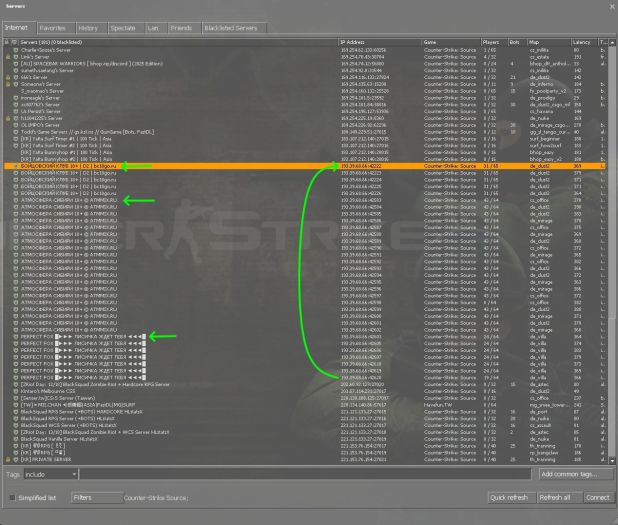 |
| The fake servers from ATMMIX.RU - the worst offender in CS:S for fake servers and scams |
Now you have more IPs to ban and this group seeing it's a bad one use a decision maker to use an IP range ban instead...
193.39.68.0 for the in game list
193.39.68.0/24 for the windows firewall list type
The decision maker here to block using a IP Range and not just a single IP...
Blocking a IP range in the windows firewall knocks out 254 other IP's they may use tomorrow, or next week.
In CS:S if your IP range blocks get to around 150 or so... every week there may be one or two more.
The more IP ranges you block the less choice in IP's to abuse they have.
Reddit. (CSS only) A better way to get rid of spam servers (2023 henk717) Another windows firewall method.
GitHub steamserverspamfilter An updated Firewall list Aug 2025 from the above reddit post. This list is single IP's and has 1,382 individual IPs.
GitHub goldsrc-fake-servers-firewall Another Windows firewall effort. These are great but it is only as good as a updated list. His article on it.
Inserting "tags" into Source 1 game server browsers can filter lots of bad servers.
Here are the definitions of some I know of and you can experiment with them to see if they reduce your list.
Counter-Strike: Source (CS:S) Tag List
no-steam, nosteam, nonsteam, fox, perfect, ru, naykon, v34, v93, 1mpulse, LKv2, blocker_passes, fastpath
| Tag | Meaning and use |
| no-steam, nosteam, nonsteam | Cracked server setups; often used by spoof infra to attract non-Steam clients. |
| fox, perfect | Bait tags mimicking popular mod packs; reused by SGaming and others. |
| ru | Russian region/language tag; common in SGaming and AIMMIX spoof clusters. |
| naykon, (or even just nay) | SGaming signature; filtering by this tag can halve the server list. |
| v34, v93 | Version identifiers; spoof servers use these to appear compatible with older clients. |
| 1mpulse, LKv2 | Custom mod/server pack identifiers; often reused by spoof infra. |
| blocker_passes | Indicates spoof logic that bypasses browser filters. |
| fastpath, sgaming, aimmix | Known scam group; Bot heavy servers often redirect or trap players with a ban/donation also you may include sgaming and aimmix. |
Team Fortress 2 (TF2) Tag List
bot, idle, trade, SGaming, redirect, clean, milestone, fastpath
| bot | Indicates bot presence; often used by spoof servers to simulate activity. |
| idle, trade | Common bait tags; spoof infra mimics idle/trade servers to attract players. Can block wanted and unwanted servers |
| SGaming, AIMMIX | Signature of Russian spoof infra group; often paired with redirect logic. |
| redirect | Server will forcibly move players to another IP or game mode. |
| clean | Used by admins to mark verified, spoof-free servers. |
| milestone | Tag used to mark rare clean windows or suppression events. |
| fastpath, (also sgaming, aimmix) | Known scam group; Bot heavy servers often redirect or trap players with a ban/donation also you may include sgaming and aimmix. |
Designed by INsane Webmaster - dodbits.com using Template Toaster (Joomla! Version 4)
